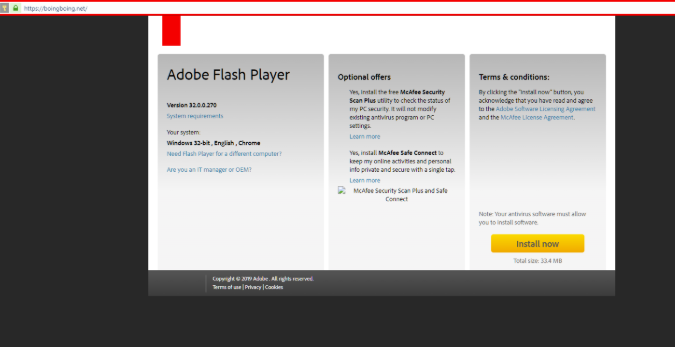
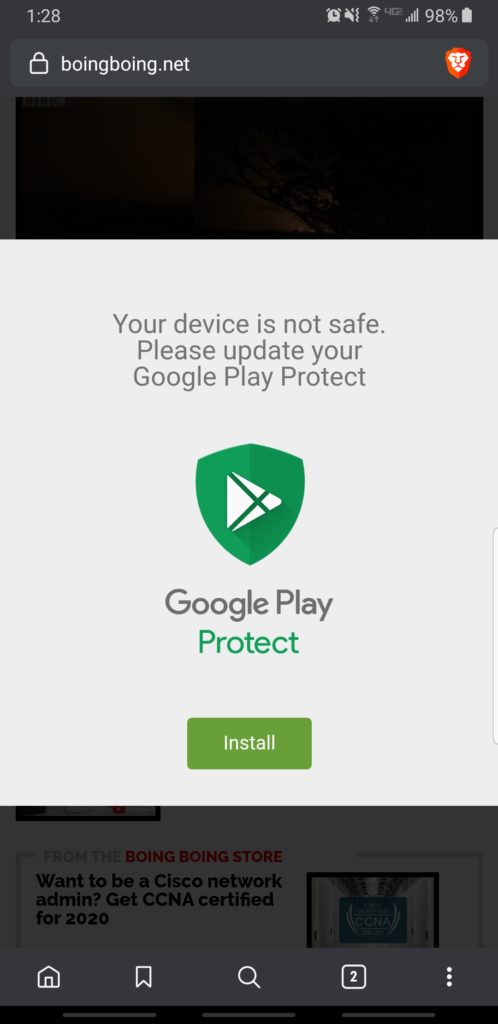
During the weekend BoingBoing readers reported strange unclosable pop-over ads that instructed visitors to install Google Play Protect. Some popups were telling users that their Google Protect needs updating and other pop-up ads were telling users that they should install Adobe. After clicking the Install button users are redirected to the fake Adobe flash Install page that instructed users to download Adobe Flash Player at this particular URL – h**ps://flashpliayers.****/software/download.php?key=Fp38.46.544775
Other user reported that the downloaded .exe file shows a strange .txt file that we can see at Pastebin . The same user said that it seems that hackers used 7z SFX Constructor from this site http://usbtor**ru/viewtopic.php?t=798 the exe sends a request to ***430lodsposlokstore
Today BoingBoing reported that their site was indeed hacked during the past weekend. In their statement they asked visitors to run local AV s or malware canning software.
In the statement they said that-“An unknown party logged into Boing Boing’s CMS using the credentials of a member of the Boing Boing team.”- after which “They proceeded to install a widget into our theme that allowed them to redirect users to a malware page hosted at a third party.”
BoingBoing also said that the malware, even though it was acting like an ad, it did not come from the company serving ads. But “it did allow our ad partner to eventually notify us of the specifics of the attack.”. BoingBoing did not explaing how come their ad partner became aware of the specifics of the malware.
After that they were able to “track down the malicious activity and user account in question and react accordingly”, and added that “Even two-factor authentication and password hygiene can be compromised on the user’s end,”.
According to BoingBoing admin (orenwolf) “no user data was leaked”.